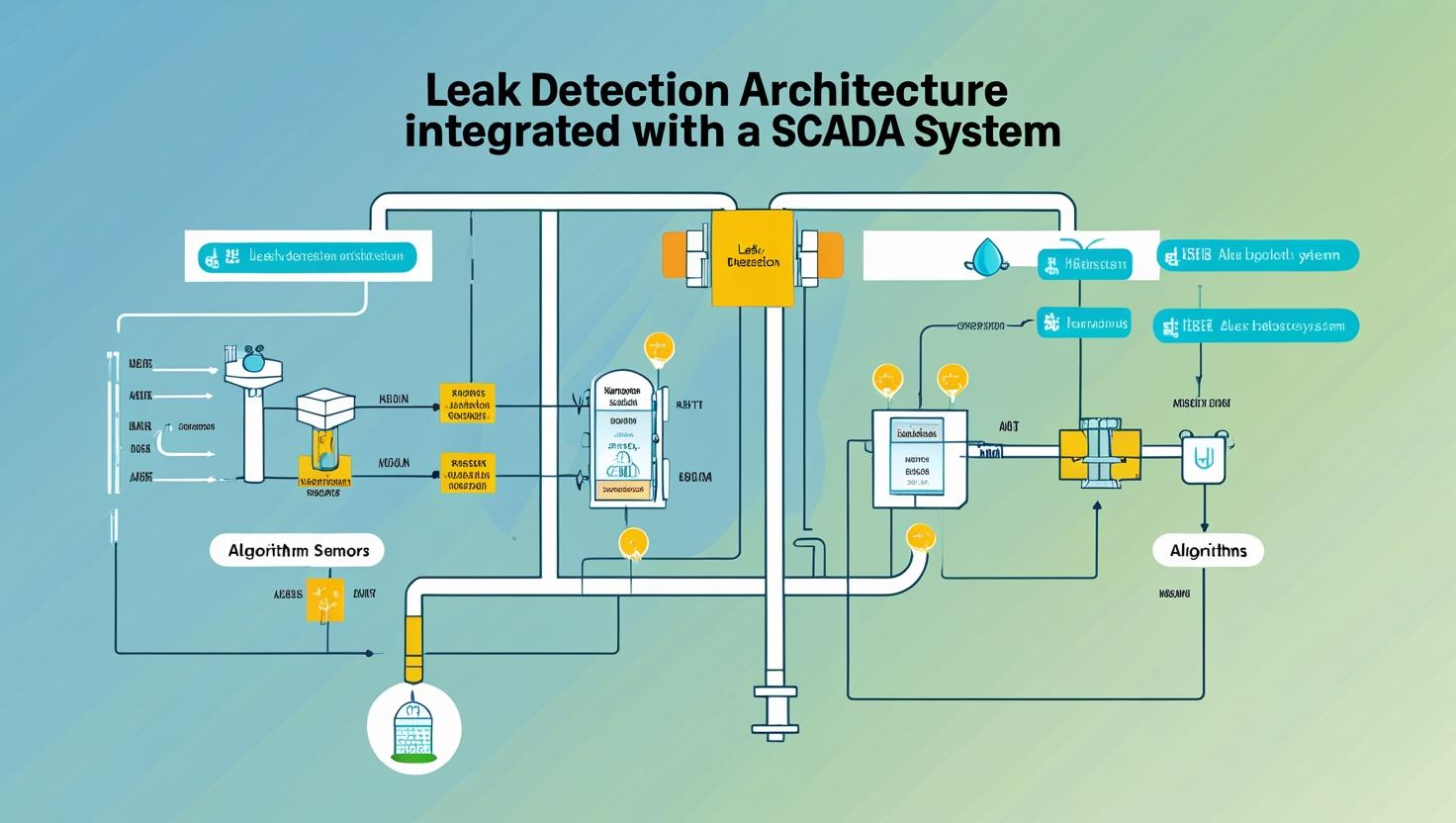
Your SCADA system wasn’t designed for leak detection, but it holds the keys to making it possible.
Operators and integrity teams face a common dilemma: how do you implement high-performance leak detection when you’re limited by the data frequency, resolution, and structure of an existing SCADA environment?
Retrofitting a leak detection system into this reality requires more than plugging in an algorithm, it demands a thoughtfully engineered architecture that works with your constraints, not against them.
The good news? You don’t need to displace your SCADA to achieve strong leak detection performance. With the right approach, you can layer advanced analytics, compensate for telemetry gaps, and build a system that’s both practical and effective.
In this post, we break down what it takes to build a robust leak detection architecture around your SCADA system. From meter strategies to data alignment to alarm configuration, you’ll walk away with a clear framework to guide implementation, and confidence that your infrastructure is leak detection–ready.
1. The Reality of SCADA in Leak Detection
Let’s start with the fundamentals: SCADA was built for control, not detection.
SCADA systems were originally developed to monitor equipment status and enable remote control of pumps, valves, and compressors. Leak detection, however, requires more precision. It demands timely, consistent, and reconciled flow and pressure data to detect anomalies, quantify losses, and pinpoint location.
Common SCADA Limitations:
-
Low reporting frequency: Many SCADA systems report every 1, 5, or even 15 minutes, not ideal for timely detection.
-
Latency and polling delays: Time skew between field devices introduces uncertainty into leak signatures.
-
Inconsistent instrumentation: Orifice plates, turbine meters, or ultrasonic sensors may vary in accuracy or calibration.
-
No built-in analytics: SCADA doesn’t interpret trends; it reports raw values.
Yet, despite these challenges, SCADA remains the single richest source of pipeline data, and the backbone of pipeline visibility.
The challenge is to architect a leak detection system that integrates with it intelligently.
2. Key Components of a SCADA-Centric Leak Detection Architecture
Building a leak detection system around SCADA doesn’t mean compromising on performance. It means engineering every layer, from data acquisition to alarm logic, with a clear understanding of your constraints and goals.
Let’s walk through the major components:
a. Flow and Pressure Meter Strategy
The foundation of any leak detection system is meter quality and placement.
Best practices:
-
Dual-metric inputs: Use both flow and pressure measurements whenever possible. Flow alone does not give the full picture.
-
High-accuracy meters at segment ends: Coriolis and ultrasonic meters provide better resolution than orifice or turbine types.
-
Meter calibration routines: Ensure that meters are validated and corrected over time, especially after process changes or batch events.
Key consideration: If replacing meters isn’t an option, statistical models can be used to extract greater insight from existing instrumentation, such as correcting for expected drift or applying digital filtering.
b. Data Alignment and Time Synchronization
Data misalignment is the silent killer of leak detection accuracy.
Leaks are identified by detecting discrepancies in flow or pressure over time. If your inlet and outlet meters are reporting at different intervals or are out of sync by even 30 seconds, detection fidelity suffers.
Solutions:
-
Implement a data pre-processing layer that interpolates, synchronizes, and normalizes timestamp differences across all incoming data.
-
Use integrated values for long-interval data to simulate continuous flow.
This is especially important when polling intervals are 5–15 minutes, which is common in remote assets or older telemetry networks.
c. Choosing the Right Leak Detection Method
Leak detection algorithms vary in complexity and sensitivity. Selecting the right method depends on your SCADA data quality and system constraints.
Common approaches:
-
Compensated Volume Balance (CVB)
-
Compares inlet and outlet volumes over time, adjusted for inventory changes.
-
Works well with longer polling intervals.
-
Can detect leaks down to ~0.5–1.0% of flow rate with tuned instrumentation.
-
-
Statistical Process Control
-
Monitors deviation patterns from baseline to detect leaks probabilistically.
-
Effective for noisy data or systems with frequent transients.
-
-
RTTM (Real-Time Transient Modeling)
-
Physics-based modeling of pipeline behavior.
-
High accuracy but computationally intensive; requires two (2) or more intermediate pressure measurements, accurate physical models and frequent data.
-
-
Hybrid/Ensemble Methods
-
Combine volume balance with statistical and/or RTTM.
-
Offers high sensitivity with noise tolerance, particularly in mixed-instrument pipelines.
-
Recommendation: For most operators integrating with SCADA, a hybrid architecture using volume balance as the base layer and statistical filtering for noise suppression provides the best balance of sensitivity and deploy ability.
d. Alarm Logic, Confidence Scoring, and Visualization
Once detection models are in place, the next challenge is to ensure alerts are:
-
Timely
-
Trustworthy
-
Actionable
What to implement:
-
Multi-tier alarm levels: Notification → Warning → Alarm
-
Confidence scoring: Quantify certainty of a leak based on detection metrics, time under threshold, and signal persistence.
-
Event visualization: Use control room dashboards or web portals to display alarm location, severity, and historical trends.
-
False alarm filters: Include known events (pig launch, valve transition) to avoid nuisance alarms.
By contextualizing alarms, you help operators respond faster, and reduce fatigue.
e. Forensics and Reporting Infrastructure
Regulators increasingly expect operators to document not just that a leak was detected, but how.
Your leak detection architecture should include:
-
Data archiving: Store raw and processed data for months or years.
-
Leak event logs: Timestamped logs of detection, operator response, and resolution.
-
Replay tools: Graphical or tabular playback of pipeline state before, during, and after alarms.
These elements are critical for:
-
Internal incident reviews
-
Regulator audits
-
Continuous tuning and model improvement
3. Real-World Deployment Considerations
It’s not enough to have a theoretical design. Implementation in the field brings its own challenges. Here are key considerations and strategies:
a. Long-Interval SCADA Reporting (ie. 15-Minute Data)
Pipelines in remote areas often have cellular or satellite telemetry that limits data update intervals.
Mitigation tactics:
-
Use integrated values (ie. cumulative volume) rather than point samples.
-
Apply statistical methods over wider time windows.
-
Accept reduced detection speed (ie. 30–45 minutes) while maintaining sensitivity.
Case in point: Even with 15-minute data, some systems can reliably detect 2-3% leaks within 30–45 minutes, far better than detecting nothing at all.
b. Data Quality and Noise
Field data is rarely perfect. You may have:
-
Orifice meters with limited accuracy
-
Turbine meters affected by wax or sand
· Pressure sensors showing drift or offset issues
Approach:
-
Use data normalization routines
-
Apply filtering (ie. Kalman filters or Wasserstein metrics) to reject outliers
-
Combine multiple sensor inputs where possible (ie. dual flow meters or pressure sensors)
c. Training and Change Management
Operators may not trust a new system, especially if they’ve been burned by false alarms before.
Build trust by:
-
Involving control room personnel in alarm tuning
-
Running leak simulations and table-top exercises
-
Gradually integrating alarms into operations as confidence builds
Remember: Operator engagement is just as important as algorithm performance.
d. Regulatory Alignment
Different jurisdictions (API RP 1130, CSA Z662 Annex E, PHMSA 49 CFR 195.134/.444) have different leak detection expectations.
Ensure your SCADA-based architecture can:
-
Provide documented proof of sensitivity, reliability, and detection time
-
Archive leak test data (planned and blind)
-
Produce auditable logs of alarms and responses
-
Align with recommended practices, even if the pipeline is exempt from certain mandates
4. The Future: Enhancing SCADA-Based Detection with AI and Cloud Infrastructure
Leak detection architecture doesn’t have to stop with local data and basic models.
Many operators are now layering:
-
Cloud-based dashboards for remote monitoring and collaboration
-
AI-based trend recognition to reduce false positives
-
Predictive diagnostics to detect pre-leak conditions (ie. pressure decay near slack zones)
-
Edge-to-cloud architectures for better resolution without overloading telemetry networks
The key is to treat SCADA as your foundation, not your ceiling.
Conclusion: You Can Build Strong Leak Detection Around Your SCADA
A high-fidelity leak detection system doesn’t require a full rip-and-replace of your SCADA infrastructure.
With smart architecture, you can:
-
Leverage existing meters and telemetry
-
Synchronize noisy, long-interval data
-
Layer in robust leak detection models
-
Deliver alerts that operators can trust
-
Stay compliant and audit-ready
The result? Faster detection, fewer surprises, and greater operational confidence, built on the infrastructure you already have.
Looking to build or upgrade a leak detection system that fits your SCADA reality?
At Pipewise, we specialize in designing fit-for-purpose leak detection architectures around real-world SCADA constraints, from remote telemetry and low-frequency polling to legacy meter networks.
👉 Book a free technical consult and we’ll walk through your pipeline configuration and identify the right approach to maximize detection speed and reliability, without costly overhauls.